In this article, I explain how you can use your own certificate template naming scheme, replacing the default names that are used by FAS. FAS high availability is also briefly explained.
Two challenges you may face when deploying FAS for a customer:
- Customers have a specific naming scheme for certificate templates deployed via Active Directory Certificate Services, so the default names that FAS uses are unwanted. In this case, it is possible to create your own templates, define your own names, and then instruct FAS (via PowerShell) to use those instead.
- Customers have a need for their services to be highly available. As such, you may also be tasked with configuring the FAS component to be highly available, which is quite simple given it acts in an active/active mode.
How to create FAS certificate templates with your own naming scheme
By default, FAS publishes three certificates to ADCS:
- Citrix_SmartcardLogon
- Citrix_RegistrationAuthority_ManualAuthorization
- Citrix_RegistrationAuthority

To create your own names, you can simply duplicate each of the three templates listed above: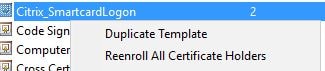
Specifying the name of the template is performed on the General tab. Repeat this step for all three templates.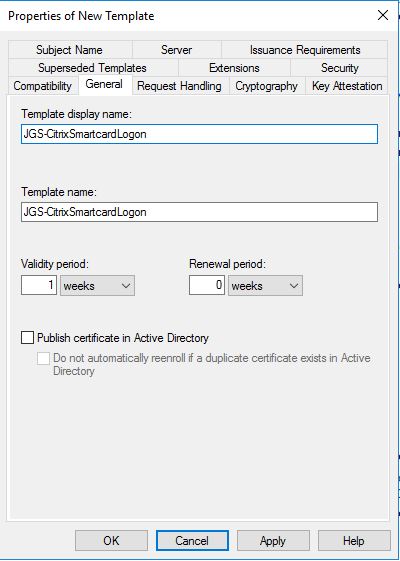
Adjust the xxSmartcardLogon certificate permissions so that each FAS server in your deployment has Enroll permission, and Authenticated Users have Read permission.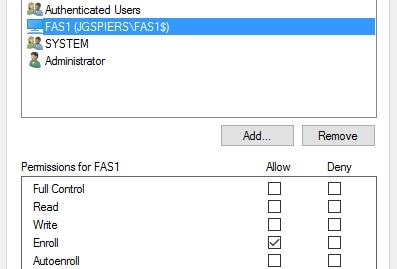
Under Certificate Templates in the ADCS console, you can delete the default issued FAS templates.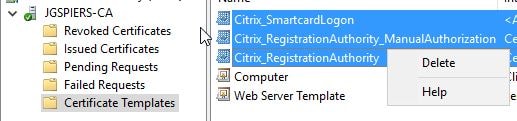
Then issue the new certificates via the ADCS console.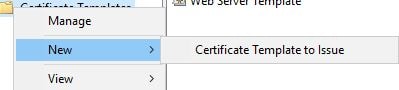
Next on your FAS server, launch PowerShell and run the below commands, replacing values with your own where appropriate:
- asnp Citrix.Authentication.FederatedAuthenticationService.v1
- New-FasAuthorizationCertificate -Address FAS1.jgspiers.com -CertificateAuthority DC.jgspiers.com\JGSPIERS-CA -CertificateTemplate “JGS-Citrix_RegistrationAuthority” -AuthorizationTemplate “JGS-CitrixRegistrationAuthority_ManualAuthorization”
Note: Take note of the Id from the console output, as we will use that in a near-future step.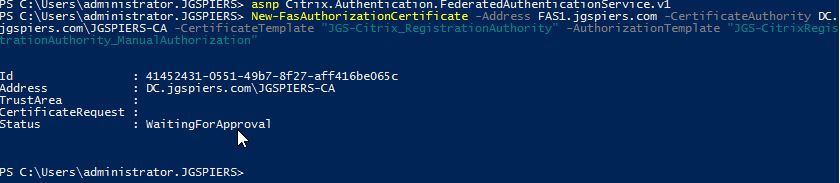
This step allows the FAS server to send a certificate request for the Manual Authroization certificate to your Certificate Services server. This is a temporary certificate that is valid for 24 hours by default. The CA will not issue the certificate automatically, hence the need to manually issue it from the CA console. Log on to your CA console and issue the pending certificate request.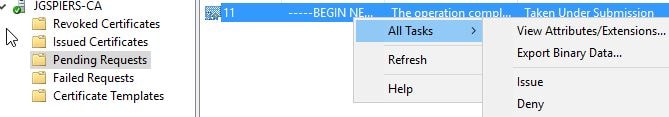
Once the certificate is issued, FAS uses the Manual Authorization certificate (JGS-CitrixRegistrationAuthority_ManualAuthorization) to automatically obtain the Registration Authority certificate (JGS-Citrix_RegistrationAuthority), which is valid for 2 years by default. The FAS server then deletes the Manual Authorization certificate (JGS-CitrixRegistrationAuthority_ManualAuthorization) as soon as it has a Registration Authority certificate (JGS-Citrix_RegistrationAuthority).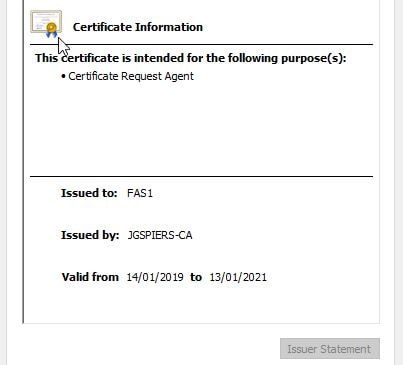
Any further Registration Authority certificate renewal will use the Citrix_RegistrationAuthority certificate template, thus you can unpublish the Citrix_RegistrationAuthority_ManualAuthorization template from AD CS if you wish.
Next run the following command:
- Get-FasAuthorizationCertificate -Address FAS1.jgspiers.com
Note that two Authorization Certificates appear. The default one when you originally deployed FAS and pushed the default certificate templates out, and the new one you just enrolled for.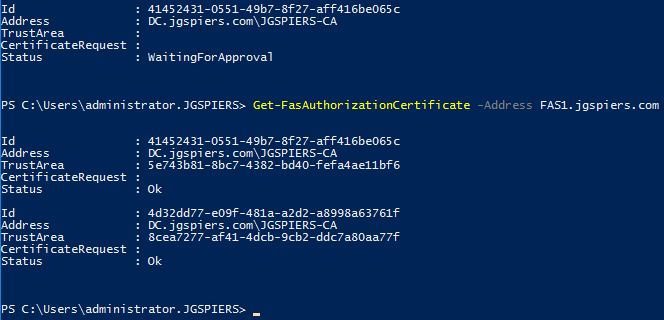
Using the Id value that you captured in an earlier step, we can identify which the other default Authorization Certificate by its Id, which we want to delete. Run the following command, replacing values with your own where appropriate:
- Remove-FasAuthorizationCertificate -Address FAS1.jgspiers.com -Id 4d32dd77-e09f-481a-a2d2-a8998a63761f
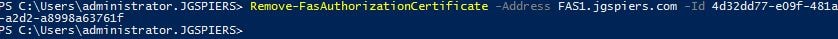
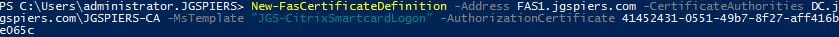
Using the Id value that you captured in an earlier step, run the following command, replacing values with your own where appropriate:
- New-FasCertificateDefinition -Address FAS1.jgspiers.com -CertificateAuthorities DC.jgspiers.com\JGSPIERS-CA -MsTemplate “JGS-CitrixSmartcardLogon” -AuthorizationCertificate 41452431-0551-49b7-8f27-aff416be065c
You can view the new Certificate Definition by running the following command:
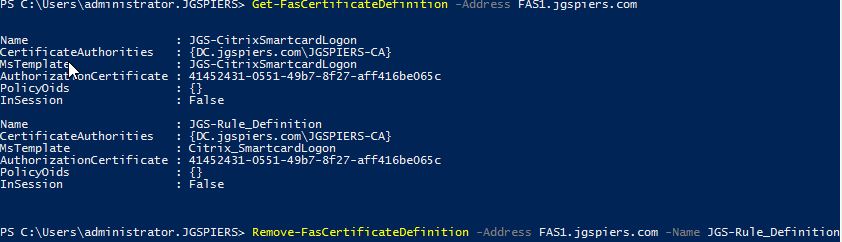
- Get-FasCertificateDefinition -Address FAS1.jgspiers.com
Note: If you see more than one Certificate Definition here, you will probably want to delete them. For example, the default definition may appear if you have already created a FAS rule.
The next step involves creating a FAS rule, which will link permissions to your newly created Certificate Definition. Open the Federated Authentication Service Configuration console and browse to the User Rules tab. Click on Add.
Specify a name and then click Ok.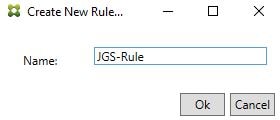
Using the drop-down, select your Certificate Authority.![]()
Using the drop-down, select the Citrix_SmartcardLogon default certificate template. We will later use PowerShell to change this to the template we created earlier.![]()
Configure other settings as desired. The configuration of each remaining item is explained in more detail here
Click Apply.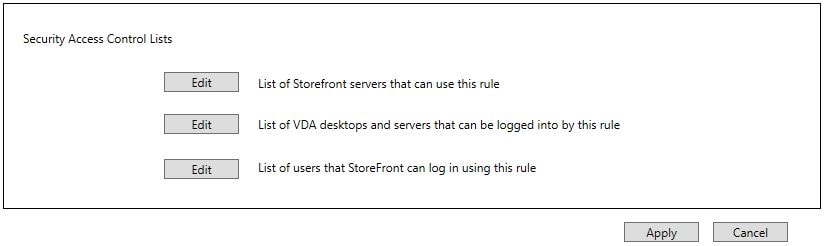
Now run the following command:
- Get-FASRule -Address FAS1.jgpiers.com
Notice the FAS rule that has been created. You now need to change the Certificate Definition to the one you created earlier. To do so, run the following command, replacing values with your own where appropriate: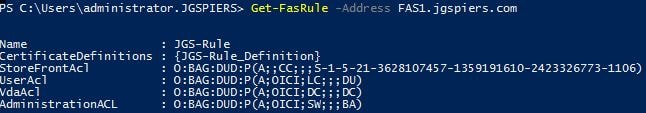
- Set-FasRule -Address FAS1.jgspiers.com -Name JGS-Rule -CertificateDefinitions JGS-CitrixSmartcardLogon
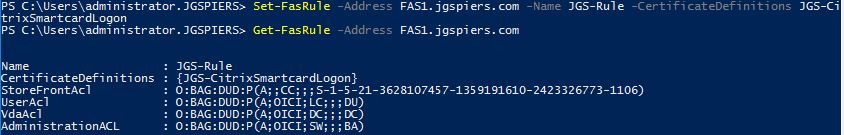
To clean up the Certificate Definition that was created by the Federated Authentication Service Configuration GUI, run the following commands, replacing values with your own where appropriate:
- Get-FasCertificateDefinition -Address FAS1.jgspiers.com
- Remove-FasCertificateDefinition -Address FAS1.jgspiers.com -Name JGS-Rule_Definition
Finally, create a Group Policy that applies to your StoreFront servers and informs them of the new FAS rule you have created.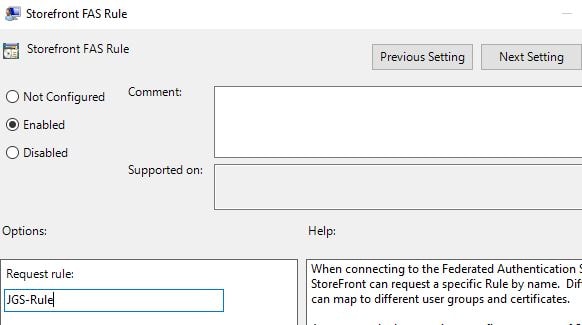
Reboot your StoreFront servers so they pick up the new rule. A gpupdate via CMD is not enough.
You can tell when the rule has been picked up by StoreFront by looking at the HKLM\SOFTWARE\Policies\Citrix\Authentication\UserCredentialService registry key.
For high availability, you simply perform the same steps on your additional FAS servers, to make sure the configuration is the same. As previously mentioned, FAS works in an active/active mode. Be sure to update the Federated Authentication Service Group Policy setting by clicking Show beside DNS Addresses.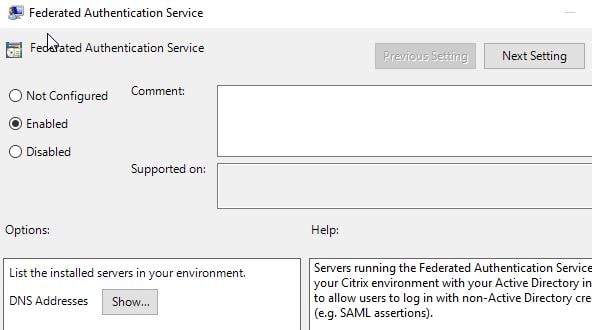
Enter the name of each FAS server you want to use. Click OK.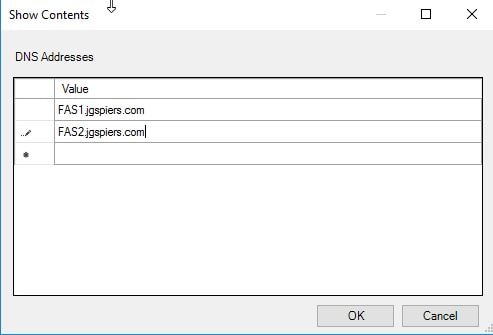
Satish
March 15, 2019Hi Carl,
We have a FAS environment setup recently. While I was going through my FAS configuration We found that for “Get-FasAuthorizationCerticate -address fas.domain.com” status is showing “MaintenanceDue”. Please let me know what are the steps we must do to bring that back to status “OK”
George Spiers
March 18, 2019According to Citrix the MaintenanceDue status is harmless and can be ignored, but it has been fixed in the latest FAS release.
Srini
August 2, 2019Hi,
Do we need to enable the “Follow the settings in the certificate template if applicable. Otherwise, automatically issue the certificate” option in the CA Server in order to automatically issue the user certs without admin intervention? Is this mandatory?
George Spiers
August 18, 2019Correct.
rajneesh
January 3, 2020Kinldy let us know the Process to add SHA2 certificat..
Khanh
April 17, 2020for the second fas server do we have to redeploy the templates?
A.D.
June 10, 2020Good question!
George you wrote “For high availability, you simply perform the same steps on your additional FAS servers, to make sure the configuration is the same” but does this mean all certificates have to deploy again?
Are not different certificates stored in the Microsoft CA? Or do I have the possibility to select the existing certificates when I use the wizard? With the authorization for the Citrix FAS against the Microsoft CA I understand that another certificate has to be used but with the others it doesn’t make sense, does it?
George Spiers
September 7, 2020Nope just deploy once.
Michael Hagberg
November 18, 2020A wuestion about this. Finally, create a Group Policy that applies to your StoreFront servers and informs them of the new FAS rule you have created.
Where do you find that policy rule and where did you name your FAS rule?
Sourabh Jain
April 14, 2021Hi,
I am looking to configure certificate-based authentication on the application so that it can use FAS in-session certificate for SSO. Do you’ve any guidelines for such configuration required on the application side?
Regards,
Sourabh
Saju P V
October 12, 2021Hi
I would like to know how we can configure multiple FAS servers in each azure region.
Say in east us 2
South east asis 2
etc.
Do we need to make any HA or LB configuration? Also when we configure second FAS server, do we need to deploy and publish the certs again? I guess its already done so we just need to authorise?
Many Thanks
Saju