One of the requirements of using Receiver for HTML5 internally with HTTPS StoreFront sites is to encrypt the ICA connection rather than using clear text. This is a requirement since all modern browsers do not support unencrypted Web Socket connections from an HTTPS site which Receiver for HTML5 uses.
When you make a connection to Receiver for HTML5 the ICA/CGP (Session Reliability) protocols are wrapped inside the HTML5 protocol. Browsers do not like the fact you’re making an HTTP Web Sockets connection from an HTTPS StoreFront site. For this reason, we further encapsulate the HTML5 protocol inside SSL/TLS 443. This method ensures that a TLS/SSL connection is made from the end-client Receiver to the VDA and it’s worth noting that this is FIPS 140-2 (Federal Information Processing Standard) compliant.
Note: You must be using XenApp/XenDesktop 7.6 or later.
You can connect to published resources using Receiver for HTML5 from NetScaler or internally using HTTP StoreFront servers however when you want to connect internally using an HTTPS StoreFront server extra configuration is required:
- Certificate installed on each VDA.
- SSL enabled on the VDA.
- HDX SSL connections enabled on the selected Delivery Group.
- DNS resolution enabled on the Citrix site.
For your VDA’s to obtain certificates, you’ll need something like Active Directory Certificate Services to automate the enrolment. For persistent machines, this works just fine. For non-persistent machines that reset after reboot, you’ll need to configure a way for the machines to request a new certificate after every reboot.
For those persistent machines, use Group Policy and navigate to Computer Configuration -> Policies -> Windows Settings -> Public Key Policies -> Automatic Certificate Request Settings -> New -> Automatic Certificate Request.
 Click Next.
Click Next.  Select the Computer template. Next.
Select the Computer template. Next.  Finish. At this stage, computer certificates will enrol for every machine that receives this Group Policy. You should also configure the Group Policy setting Certificate Services Client – Auto-Enrollment to configure the renewal of expired certificates and removal of revoked certificates.
Finish. At this stage, computer certificates will enrol for every machine that receives this Group Policy. You should also configure the Group Policy setting Certificate Services Client – Auto-Enrollment to configure the renewal of expired certificates and removal of revoked certificates.  When machines receive the new Group Policy and restart they will receive a computer certificate.
When machines receive the new Group Policy and restart they will receive a computer certificate. 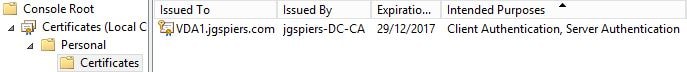 Next copy the Enable-VdaSSL.ps1 script from your XenApp/XenDesktop media’s Support/Tools/SslSupport folder to a central location, accesibly by each VDA.
Next copy the Enable-VdaSSL.ps1 script from your XenApp/XenDesktop media’s Support/Tools/SslSupport folder to a central location, accesibly by each VDA.  On the VDA, run command Enable-VdaSSL.ps1 – Enable. Followed by A to set ACLs, configure the firewall rules (TCP 443) and enable SSL to VDA. This command disables the ICA (1494), Session Reliability (2598) and WebSocket (8008) firewall rules on the VDA so that TLS connections is only possibly. You should eventually get the message that SSL to VDA has been enabled.
On the VDA, run command Enable-VdaSSL.ps1 – Enable. Followed by A to set ACLs, configure the firewall rules (TCP 443) and enable SSL to VDA. This command disables the ICA (1494), Session Reliability (2598) and WebSocket (8008) firewall rules on the VDA so that TLS connections is only possibly. You should eventually get the message that SSL to VDA has been enabled.
Note: If you have more than one computer certificate on your VDA, you must specify the certificate you want to use for SSL using the certificates thumprint. The command would then be: Enable-VdaSSL.ps1 -Enable -CertificateThumbPrint “thumbprint”
Note: If you want to specify a port other than 443 for TLS, use command Enable-VdaSSL.ps1 -Enable -SSLPort 4443 for example.
Note: You can change the minimum SSL protocol used. By default TLS 1.0 is used. Run command Enable-VdaSSL -Enable -SSLMinVersion TLS_1.2 for example. Valid values are SSL_3.0, TLS_1.0, TLS_1.1, TLS_1.2
Note: You can disable VDA SSL by running command Enable-VdaSSL.ps1 -Disable. This deletes the SSL ICA rule, and re-enables CGP/ICA and WebSocket firewall rules.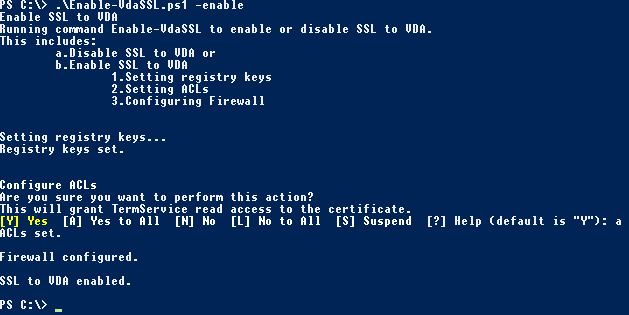 Now on your Delivery Controller, add the Citrix PowerShell snapins. Run the following commands:
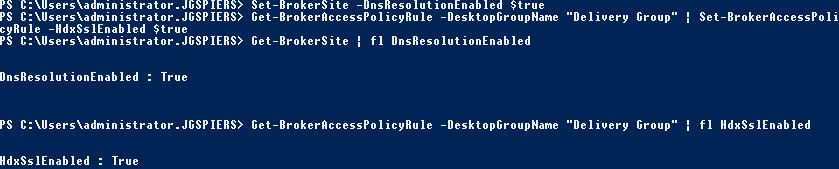
Now on your Delivery Controller, add the Citrix PowerShell snapins. Run the following commands:
- Set-BrokerSite -DnsResolutionEnabled $true – This ensures the FQDN of the VDA is passed to the client within the ICA file. The FQDN matches the computer certificate so encryption can take place.
- Get-BrokerAccessPolicyRue -DesktopGroupName “Delivery Group Name” | Set-BrokerAccessPolicyRule -HdxSslEnabled $true – This command enables SSL on the Delivery Group. You can’t enable SSL on individual machines.
On a side not if you are experiencing issues with connecting to resources using RfHTML5 you can enable logging by browsing to https://yourreceiverforwebsite.domain.com/citrix/storenameweb/clients/HTML5Client/src/ViewLog.html. Now click Start Logging.
Note: Also check the VDA’s Event Log for events generated by the TcIca. Then log on to your Receiver for Web site, start a published application and a log file is generated. It can be downloaded to text file.
Then log on to your Receiver for Web site, start a published application and a log file is generated. It can be downloaded to text file.  This is a bad working log file, where the session was unexpectedly terminated before launch.
This is a bad working log file, where the session was unexpectedly terminated before launch.  And this is a good working log file where the session was successfully established.
And this is a good working log file where the session was successfully established.  Finally after the certificate is enrolled and SSL enabled on the VDA/Delivery Controllers, I can make a successful direct connection.
Finally after the certificate is enrolled and SSL enabled on the VDA/Delivery Controllers, I can make a successful direct connection. 
The session is encrypted using TLS 1.2 and AES 256 bit encryption.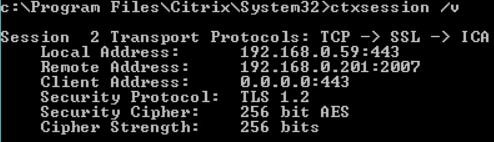
Travis
November 12, 2017How does this work with a NetScaler? I’ve seen several guides but none discuss Secure ICA with a NetScaler.
George Spiers
November 13, 2017If you have NetScaler in the mix, ICA traffic from an endpoint out on the internet to NetScaler is encryted by default. Then, ICA traffic from NetScaler to back-end VDAs is either unencrypted or encrypted depending on if you have implemented Secure ICA or not.
Travis
November 13, 2017My question was meant more along the lines of “How does NS know that the VDA is using Secure ICA”. I assume it’s in the ICA file, but I can’t find any details on this or what I should look for in my ICA file to ensure it’s there.
George Spiers
November 13, 2017Ah so yes, StoreFront ultimately produces the launch.ica file from information gathered from your Delivery Controllers. Such information contains the port on which HDX will connect on. From this NetScaler will know to establish 443 to the end-client but proxy ICA over port 1494 to the back-end for example.
Mcharm
March 30, 2023my senario is that the back end is previously SSLenable. ADC were deploy afterward. how do i go about encrypting the traffic between ADC and VDA???
David
May 7, 2023Did you find an answer to this?
I have a client that is using Big-IP APM as their external gateway. As far as I can see, it re-writes a portion of the ICA file, including the SSLProxyHost parameter which is set to :443. Now that we have Secure ICA enabled on the VDA’s, ICA connections fail, presumably because F5 doesnt know to connect to the VDA over SSL. I was searching for information on how it works with netscaler gateway in case there are similarities in how it can be resolved for F5.
Pingback: SSL connection between Citrix Delivery Controllers and VDA’s with Receiver for HTML 5 or not | Apttech's Blog
Henrik
March 22, 2018I have sessions that sometimes disconnect and they will not reconnect – using session reliability and SSL does not seem to work?
George Spiers
March 22, 2018What version of XenApp/XenDesktop?
Do the sessions drop due to a network drop or have they just randomly dropped under good network conditions? Have you ran a WireShark trace to see what could be causing the session disconnects and reconnections to fail?
SH
March 4, 2019Hey George,
How we can achive for provisioned read only machines. Having 50 + vDisk in environment and atleast two or more servers are streamed from each vDisk.
Thanks
George Spiers
March 4, 2019Hello. For non-persistent machines, each machine needs to request a certificate each time they are restarted. Automatic certificate requests (configured via Group Policy) should help, and a Scheduled Task that runs the Enable-VdaSSL script on system startup.
Eric Harrison
October 9, 2022With PVS each VDA has a unique Thumbprint, so how can I automate this process using Enable-vdassl? I won’t know the Thumbprint in advance, so I am not sure how this will work? The -CertificateThumbPrint parameter seems to be required for my environment.
JustJen
January 17, 2024You may have already solved this yourself, but came across this thread and wanted to share how we resolved this without having to use a wild card cert in my environment.
We created a scheduled task that runs with trigger event windows event log, CertificateServicesClient-Lifecycle-System EventID 1006, which is generated when certificates are enrolled/renewed that then runs a script (we use powershell) to change the permissions on the newly enrolled machine cert because that also needs to be done on new certs, retrieve the thumbprint, and update the registry and set a delay for 1 min.
We also went a little extra for troubleshooting ease and created a unique event log and send success/fails in both to it so a machine can quickly be looked at to verify if permissions were successfully changed and if thumbprint was updated in registry that we can use for visual inspection and/or have other actions and/or alerts key off of.
CEM
September 12, 2019Hello George,
For For non-persistent machines, you know how to request certificate without Group policy ?
Many thanks.
Best Regards
George Spiers
September 29, 2019No, is there a reason why you would not want to use Group Policy?
Stan
December 10, 2020Hi,
Do you have to implement VDASSL if you are running all your connections with NSGW in place to have DTLS 1.2 in use? I was looing though the documentation and it’s only states that specific cyphers are required but nothing else.
I can see that TLS 1.2 is in use but when we are trying to force DTLS 1.2 it’s only DTLS 1.0 in use.
Al
February 10, 2021Hi George,
I experience issue whilst loading session with the following error:
[Sat, 06 Feb 2021 23:00:37 GMT] SESSION:|:ICA:|:TRANSPORT:|:DRIVER:|:close with code=1006
[Sat, 06 Feb 2021 23:00:37 GMT] ERROR:|:error =error-server,error-local-access
Would appreciate any guidance n this error
Amar Honnungar
April 22, 2022Plus one, me too am getting the same error. Were you able to sort this out?
Tony
June 20, 2021Hi George,
I’m having problem while trying to let Netscaler Gateway behind Imperva WAF to protect Storefront from internet. The SSL offloading on Imperva WAF is working well. I’m able to authenticate, but when I click Desktop icon, seems like ICA cannot be proxied through Imperva, thus the connection between client (from internet) gets timeout.
Do you have any idea or solution to let this deployment model work?
Many thanks
Khanh
August 3, 2022How would this work for persistence desktop and virtual app when you have more than one cert and can’t use a wildcard for security reason. When the cert expires for each vda, the thumbprint will change and would be a nightmare to manage.