Whilst this guide specifically focuses on version 13 of ADC, many of the tweaks that secure what the ADC presents can be applied to prior or later versions. This guide shows you how to obtain an A+ rating score from SSL Labs for your Citrix ADC Gateway vServer, but applies to other vServer types.
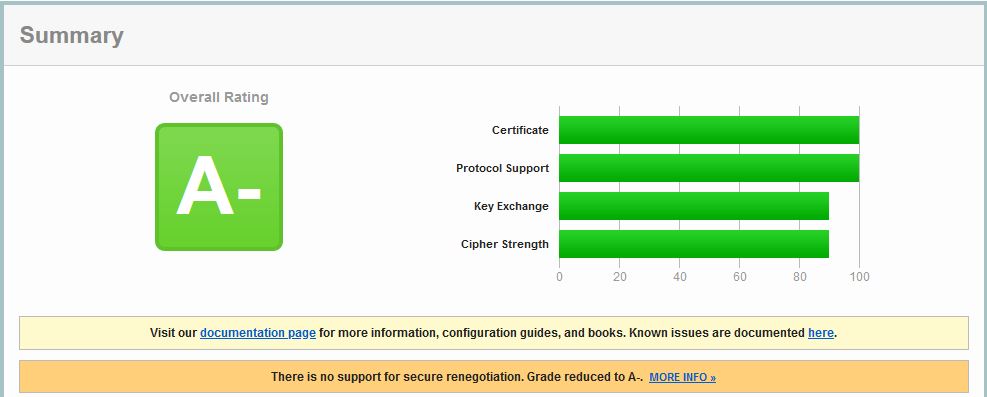
When we build a Gateway Virtual Server with default settings and run it through SSL Labs you receive a C score.
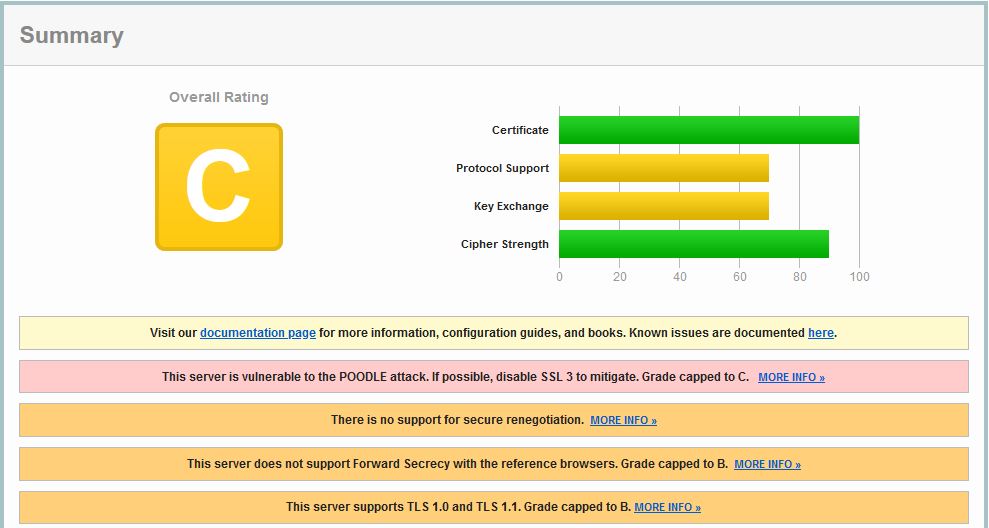
Some reasons you receive a C rating are due to SSLv3 being enabled which has various vulnerabilities, and the fact that Secure Renegotiation is not configured. Another thing to note is that all certificates in your certificate chain uploaded to ADC must be SHA2 issued.
Firstly, to improve the rating, you want to replace the default ciphers offered by the Gateway vServer with more secure ciphers. On ADC, navigate to Traffic Management -> SSL -> Cipher Groups -> Add.
Specify a Cipher Group Name and click Add.
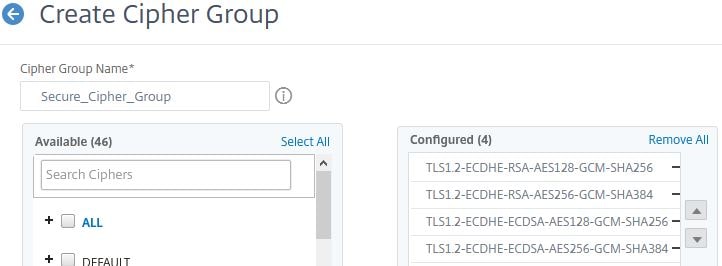
Move the following secure ciphers to the right. I’m selecting ciphers that are most secure at this time. Also note that ECDHE (Elliptic Curve Ephemeral Diffie-Hellman) ciphers include Forward Secrecy, so should always be at the top. You may need to enable some additional ciphers to support older clients such as Windows 7 or older browsers used within your organisation. Create the new Cipher Group.
- TLS1.2-ECDHE-RSA-AES128-GCM-SHA256
- TLS1.2-ECDHE-RSA-AES256-GCM-SHA384
- TLS1.2-ECDHE-ECDSA-AES128-GCM-SHA256
- TLS1.2-ECDHE-ECDSA-AES256-GCM-SHA384
Now browse to your Gateway vServer and click the pencil icon next to SSL Ciphers.
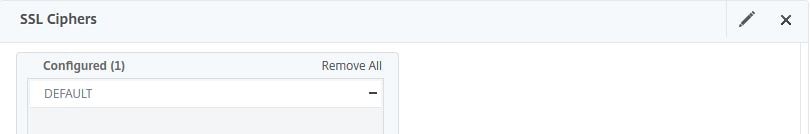
Click the minus symbol beside DEFAULT to remove it.
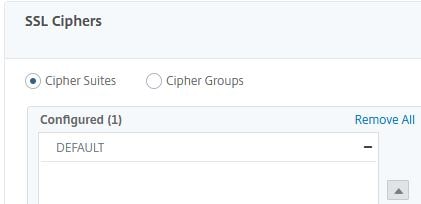
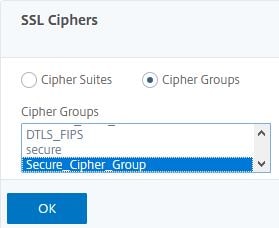
Next click on Cipher Groups and select your newly created Cipher Group from the provided list. Click OK.
You should only see your secure Cipher Group in the list. If DEFAULT is still showing, go back in and remove it again.
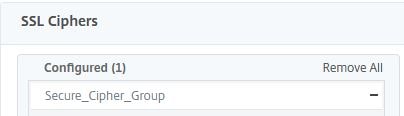
At this stage, without doing any further configuration, you will have an A- rating.
Now we will create a secure SSL Profile and bind it to the Gateway vServer. Browse to System -> Profiles -> SSL Profile -> Add.
Specify a name for your SSL Profile.
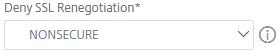
Set Deny SSL Renegotiation to NONSECURE.
Check HSTS and set Max Age to 15552000.

Under Protocol ensure that SSLv3, TLSv1, and TLSv11 is unchecked. Click OK -> Done to create the SSL Profile.
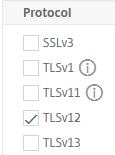
Browse back to the Gateway vServer and using the SSL Profile drop-down box, select your newly created SSL Profile then click OK -> Done.
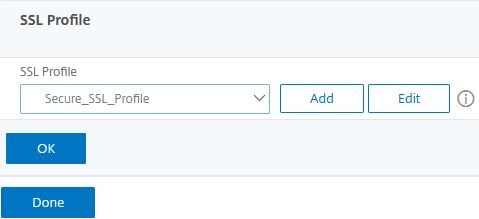
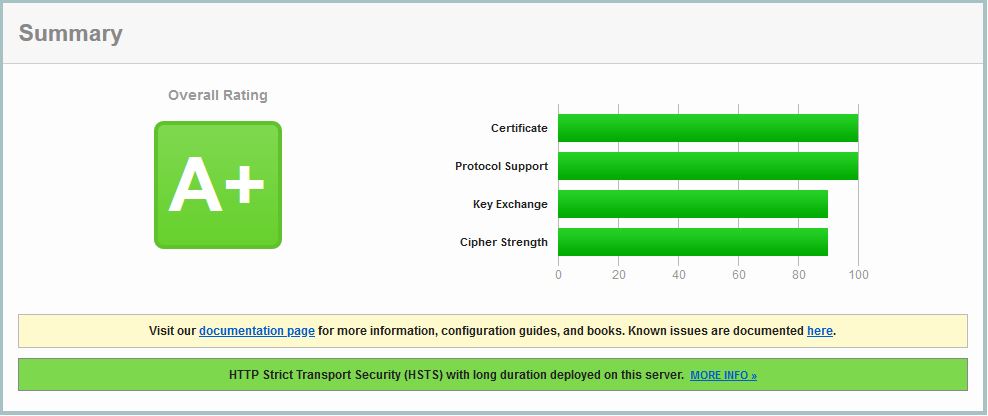
And there you have it. A+ rating on the Gateway vServer.
Davide
July 20, 2021Hello George,
good article. We configured Citrix ADC as your suggestions and SSL Qualys score is A+, but the combination Windows7-8.1/IE11 on Qualys results shows “Server sent fatal alert: handshake_failure”. How we can support these OS with right configuration?
Thank You!
Timm
July 28, 2021maybe your workspace app on client need an Update. IE11 not supported.
John H
September 1, 2021Thank you so much for this.
I do have a question, when I tick to enable HSTS in the SSL Profile as above, I get an HSTS message “Server sent invalid HSTS policy. See below for further information” and in the report “Strict Transport Security (HSTS) – Invalid – Server provided more than one HSTS header
max-age=15552000”
If I remove the tick next to HSTS in the SSL Profile, the HSTS message is “HTTP Strict Transport Security (HSTS) with long duration deployed on this server ” and I get an A+.
Is HSTS enabled anywhere else on the Netscaler?
Davide
September 2, 2021On Gateway vServer or other type? Do you have a rewrite policy also on vServer that add HSTS?
Anonymous
September 2, 2021It’s possible, I will have to check.
Ken
October 3, 2021I have the same issue; however, in a previous post (2018) there was a manual rewrite policy configuration that did the enforce STS information.
When I followed the steps and checked the HSTS + adding the value, then removed the old rewrite policy, I still only got an A rating and the following error (Strict Transport Security (HSTS) Invalid Server provided more than one HSTS header)
If I took the HSTS check and value out of the SSL profile and put the rewrite policy back in… same result, (Strict Transport Security (HSTS) Invalid Server provided more than one HSTS header) error.
I’m not sure where the issue is. I checked all Vservers and there is only 1 rewrite policy bound and that is on the Citrix Gateway.
David Rothchild
June 7, 2024hi,
its 2024, is there an update to the cipher list ? i’m assuming a few have fallen out of favour of late 😉