If you ever get authentication failures when trying to log on to NetScaler Gateway with credentials you know are correct then start logging the authentication attempts on NetScaler using aaad.debug to find out what is going wrong.
NetScaler Logon Process and Failure Reasons – https://jgspiers.com/digging-in-to-citrix-logon-process/
To enable logging, using NetScaler CLI -> type shell -> type cd /tmp -> type cat aaad.debug and press enter. (Authentication, Authorization and Auditing Deamon).
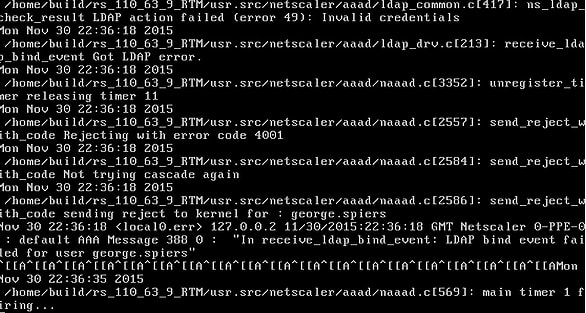
Any authentication attempts will now be displayed in the output shown above.
You can also record the output of AAA to a log file using the below command:
cat aaad.debug | tee /tmp/aaa.log
Anonymous
October 4, 2018Question…New to Netscaler troubleshooting.
With regard to the aaad.debug file and watching it for errors instead of cat’ing the file could you tail -f it to watch it?
Rob
George Spiers
October 8, 2018No because aaad.debug is not a flat file, there is nothing being logged.
Anonymous
February 17, 2020Is it possible to view this file without having “nsroot” access?
George Spiers
May 10, 2020It is yes.
Marshel Gails
December 2, 2020Is there any ways to troubleshoot shoot it using gui
Walter Scott
January 8, 2021Yes but it doesn’t always work with different browsers and versions of ADC. Stick with AAAD.debug because it never fails
Dwayne
November 15, 2021if need any account can have its RBAC edited via regex to allow shell to only do this.
ie create an allow command policy with “shell cat /tmp/aaad.debug” in it. then you should be able to online it, and no other shell commands.
Marco Schirrmeister
July 28, 2022Maybe outdated, but still worth to add a comment.
If someone really wants to do a “tail” for filtering, it is possible and you can do the following.
First shell
cat /tmp/aaad.debug | tee /tmp/aaaddebug.log
Second shell
tail -F /tmp/aaaddebug.log
TD
June 10, 2024Please add to this historical troubleshooting as well. This is only for real time. SO often we get a set of failed logins/lockouts that originated form our CAG a brute force attacks. Validating this would be great, but the nslog query is the worst!