Whilst this guide specifically uses NetScaler v11.1 many of the tweaks that secure the NetScaler configuration can be applied to prior versions or later versions. This has also been tested on NetScaler 12.0.57.24. This guide shows how to obtain an A+ rating score from SSL Labs for your NetScaler Gateway vServer.
When we build a NetScaler Gateway Virtual Server with default settings and run it through SSL Labs you get a C score.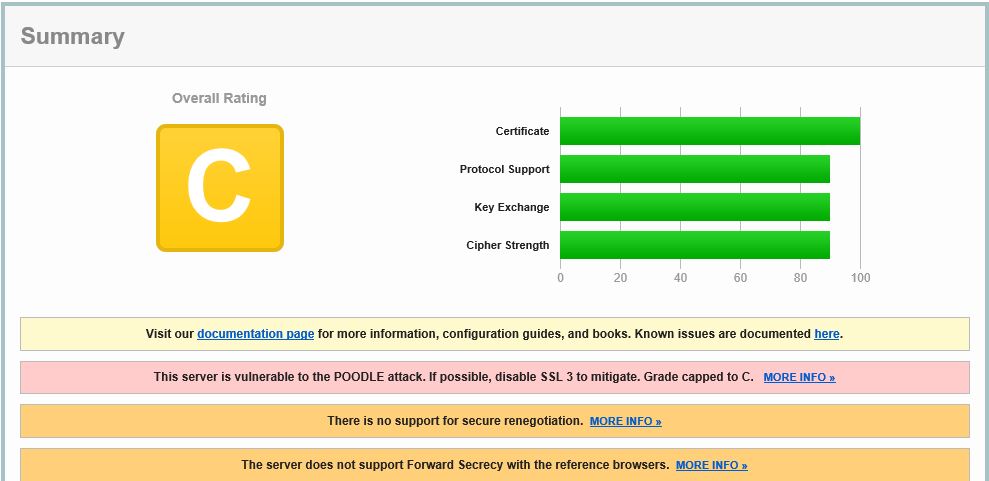
Some of the reasons you get a grade of C are due to SSLv3 being enabled which is prone to various vulnerabilities. Another reason is due to Secure Renegotiation not being available. Certificates issued to the NetScaler Gateway vServer should be SHA2 issued certificates (same applies for the intermediate certificate). Cerificates are not covered here however they do affect the score and if you are getting a grade worse than C that may be why.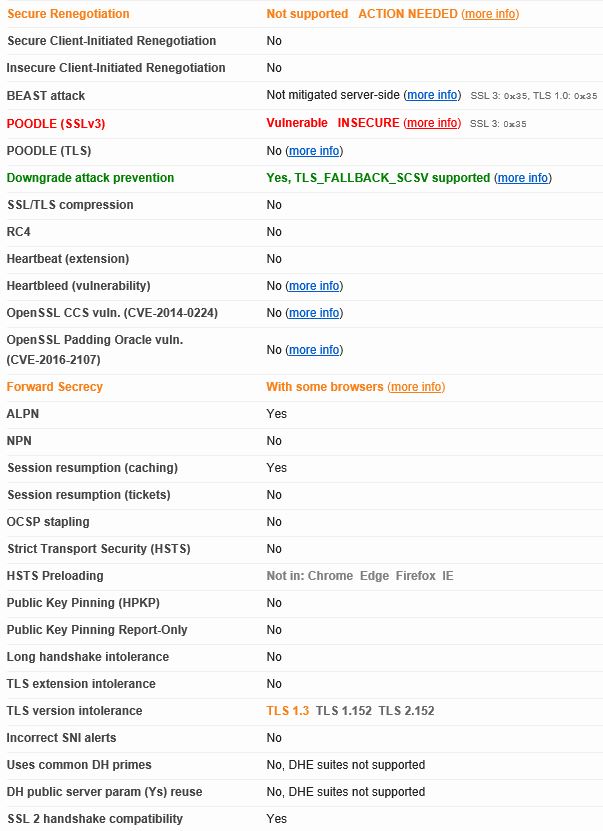
Firstly on NetScaler you want to replace the default ciphers offered by the NetScaler Gateway vServer with more secure cipher suites. On NetScaler browse to Traffic Management -> SSL -> Cipher Groups -> Add. 
Specify a name for the Cipher Group. Click Add. 
Move all secure ciphers to the right. I’m selecting all TLS 1.2 suites. You can search on the internet for a list of the latest secure cipher suites available today. Save the new Cipher Group.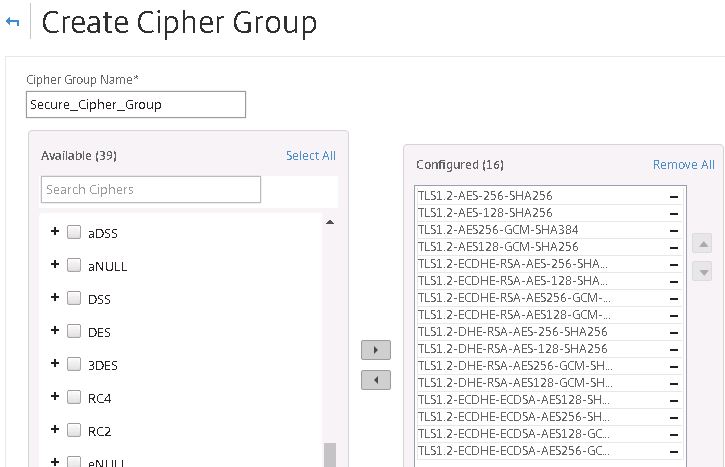
Navigate to your NetScaler Gateway vServer and click edit beside SSL Ciphers. 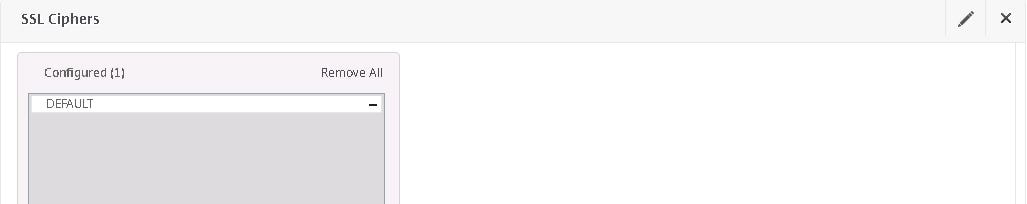
Click the minus symbol beside DEFAULT. 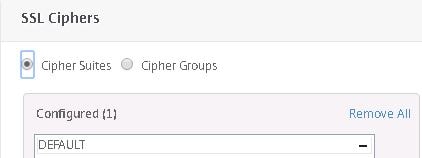
Now click on Cipher Groups. 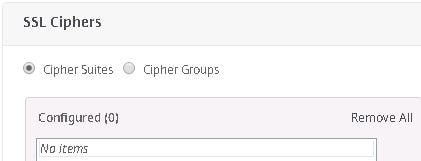
Use the dropdown to select the newly created Cipher Group and click OK. 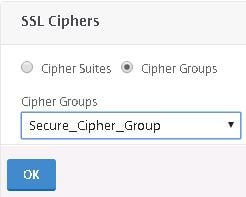
Secure_Cipher_Group is the only group you should now see in the list. If Default is still showing in the list remove it. 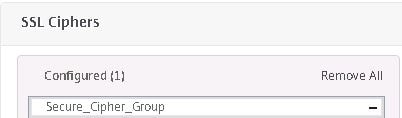
Next click edit on SSL Parameters. 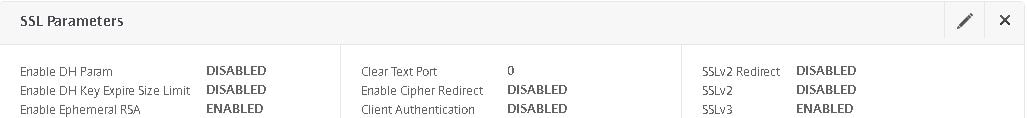
You want to disable SSL protocols such as SSLv3 so uncheck unsecure protocols.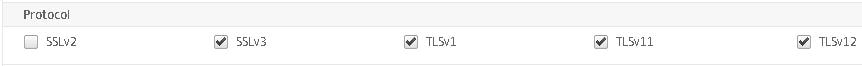
I’m leaving TLSv1.2 as the only available protocol. NetScaler Gateway will use this protocol only when negotiating a secure connection with an end-users browser. Click OK. 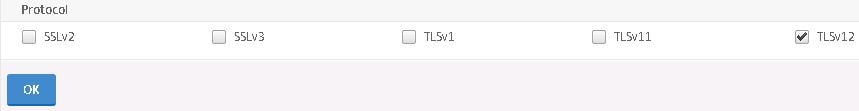
Click Done. ![]()
Now SSL Labs is reporting as A-. Still some work to do. 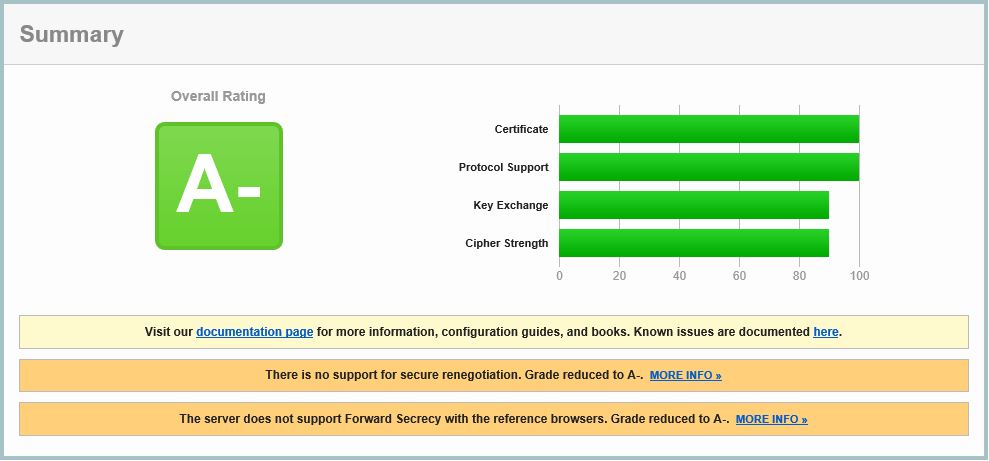
Notice that the NetScaler Gateway is no longer subject to possible attacks such as POODLE. Secure Renegotiation is still is an issue though so we will tackle that next.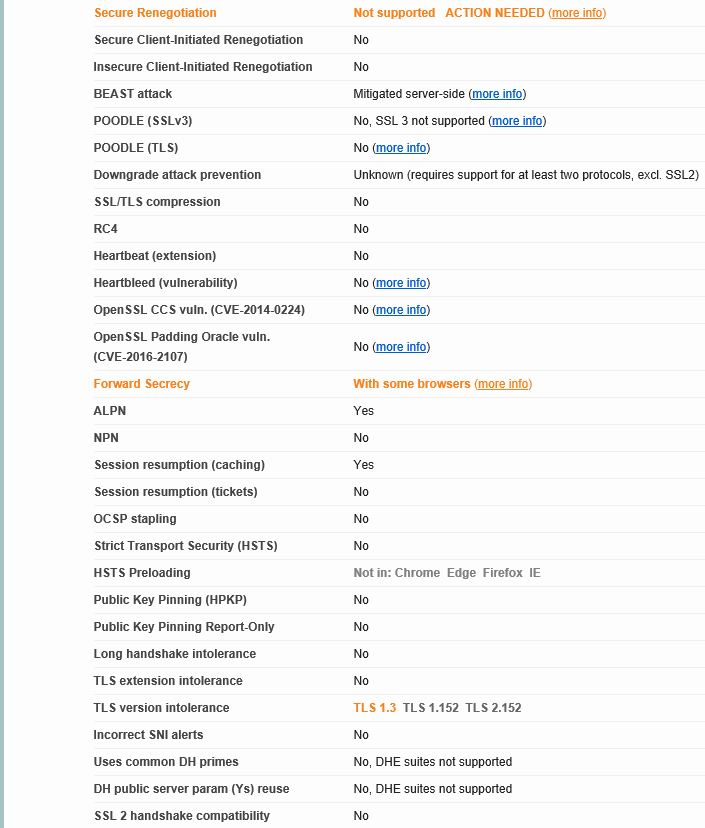
Navigate back to the NetScaler Gateway. Under SSL Profile nothing will be selected by default. Click + and add the default SSL Profile. Now click the edit button. 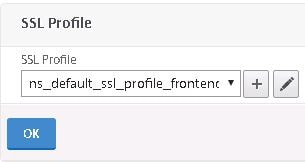
Change Deny SSL Renegotiation to NONSECURE. It should be ALL by default. Also uncheck protocols such as SSL3 from the SSL Profile. I am only allowing TLS 1.2. Save your configuration. 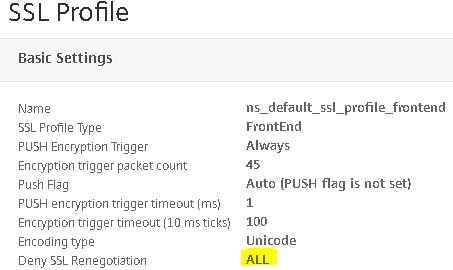
A- now but the Secure Renegotiation warning is gone. Let’s tackle Forward Secrecy next. 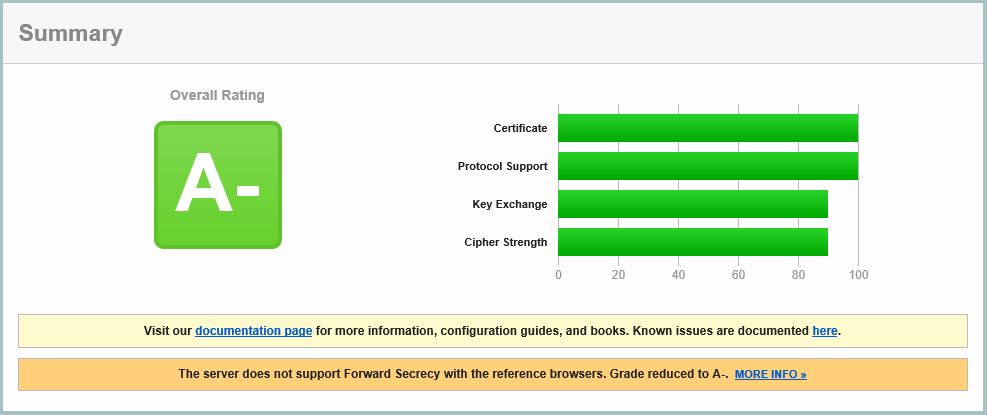
Navigate back to the Cipher Group you created earlier. You want to move all ECDHE Ciphers to the top so that the NetScaler Gateway will offer these to connecting clients first. The ECDHE (Elliptic Curve Ephemeral diffie-Hellman) ciphers include Forward Secrecy. Click OK. 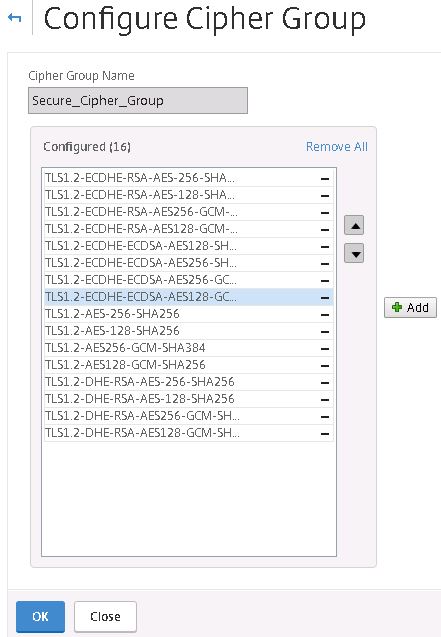
Now SSL Labs reports A. Getting there. 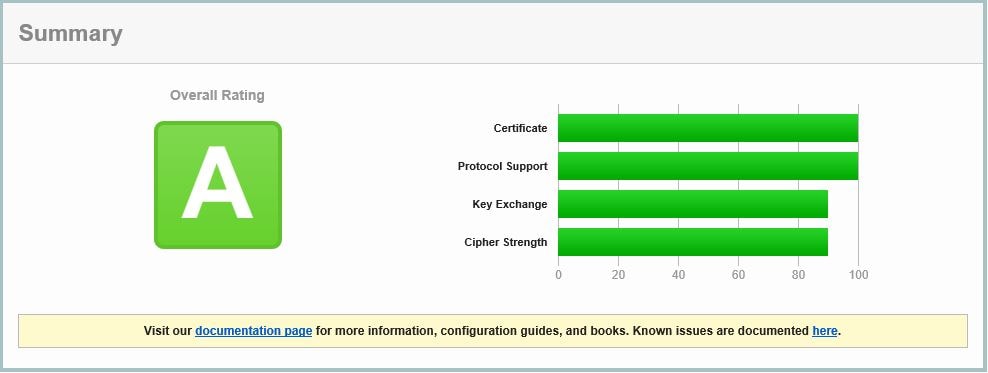
To get that A+ rating all that is left to do is to implement a rewrite action to insert a Strict Transport Security header in to the response headers.
Note: If using NetScaler 12.0 build 41.16+ you can enable HSTS directly at the vServer level under SSL Parameters or within an SSL Profile.
If you are using versions previous to 12.41.16, Navigate to AppExpert -> Rewrite -> Actions -> Add. 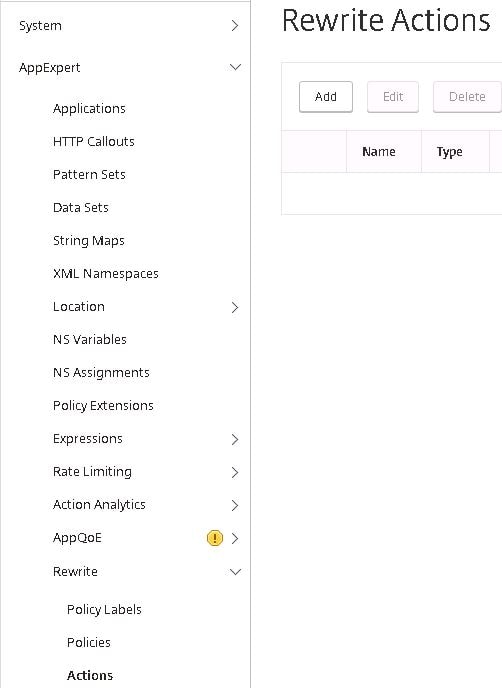
Supply a name, choose INSERT_HTTP_HEADER under Type and under Header Name type Strict-Transport-Security. Under Expression enter “max-age=157680000”. Click Create. 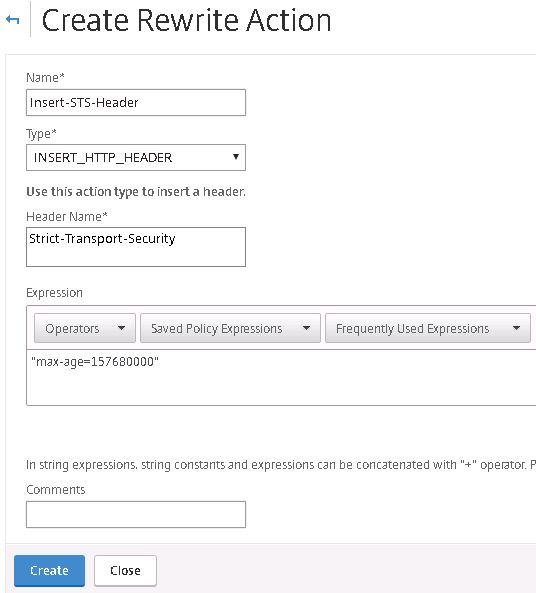
Now navigate to Policies -> Add. Supply a name, specify the action we just created and enter true under Expression. Click Create. 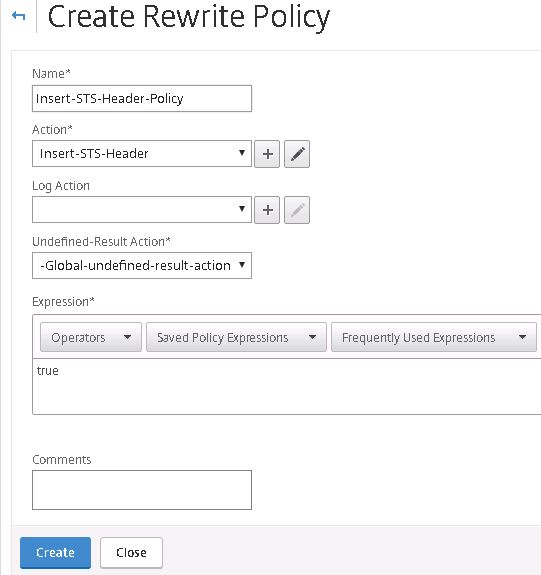
Next navigate to the NetScaler Gateway vServer, under Policies click +. 
Choose Rewrite and Reponse. Click Continue. 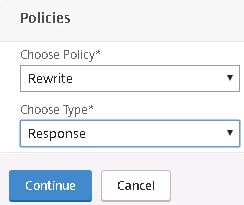
Select the Insert-STS-Header Policy. Click Bind. 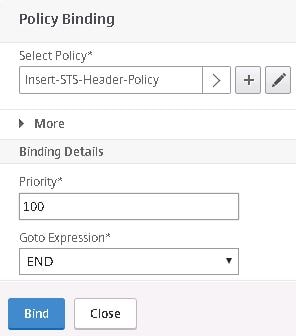
And there you have it. A+ on the NetScaler Gateway. 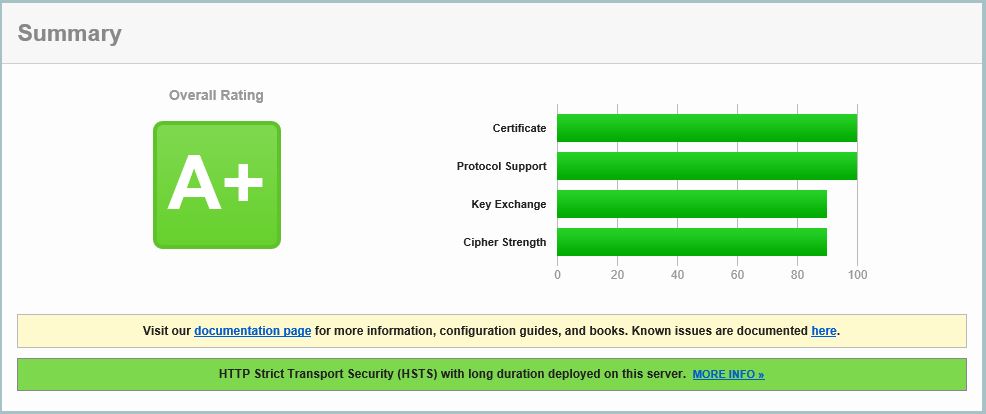
Boris Groenhout
April 25, 2017For security reasons I will advice to set the Deny SSL Renegotiation value to FONTEND_CLIENT instead of NONSECURE.
In CTX 123680 Citrix advice us to change Deny SSL Renegotiation to ALL. At least you need to change to NONSECURE, better FRONTEND_CLIENT, but ALL would be best.
George Spiers
April 25, 2017You are right. ALL is the default setting and most secure.
Pingback: Keeping your NetScaler A+ Rating on SSL Labs – Citrix and Stuff
Anonymous
June 6, 2018Hi George,
I have two problems with ns 11.1. 56.10 nc version.
I get only A-.
– All ECDHE Cipher Suits are on to the top in the CipherGroup
– when I created STS-Header-Policy with exactly expression “max-age=157680000”, the popup Expresion syntax error appears.
Juan L
June 6, 2018Hi George,
I have two problems with ns 11.1. 56.10 nc version.
I get only A-.
– All ECDHE Cipher Suits are on to the top in the CipherGroup
– when I created STS-Header-Policy with exactly expression “max-age=157680000”, the popup Expresion syntax error appears.
George Spiers
June 7, 2018Don’t copy my expression, type it in manually and it will work.
Anonymous
June 19, 2018Thanks, It’s work.
Eric
March 4, 2019Is there any drawbacks/cons to using the built-in HSTS checkbox rather than the rewrite? Does it work exactly the same way?
George Spiers
March 4, 2019It works the same way, and easier to implement of course. I did find one bug before when using the checkbox and Native OTP together. Not sure if that was fixed as I never revisited the problem and just used Rewrite as a workaround.